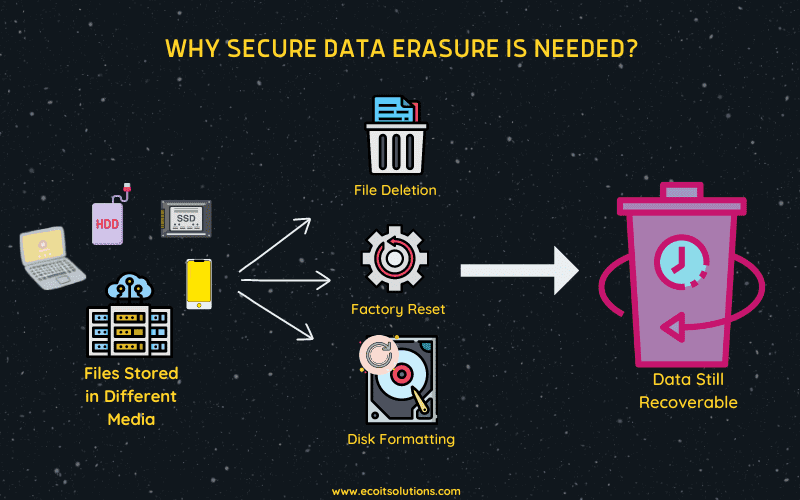
Privacy is very important. You need to make sure you keep your information safe. You should never share important details about yourself to people you don’t trust. Even if there’s no apparent threat to your data, you should still avoid leaving traces of your information anywhere. Another thing you can do to safeguard private information is to practice secure data destruction.
Any type of data that is important to you must always be secured. All information is important, but that doesn’t mean you should always keep them around. Keeping and preserving such information can become a liability to you and your company. And if this important data is no longer in use but is still confidential, you need to be smart enough to erase them.
People share and gather data every single day. You use your basic information to log in to servers and websites for personal and professional purposes. With data being passed around so freely, you need to make sure those who have access to your information are only those parties that you allow.
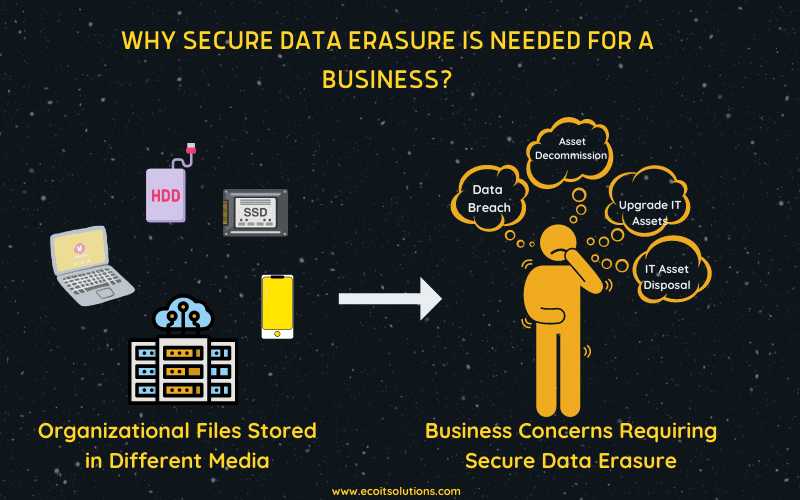
In certain cases, it becomes necessary to remove your data from certain servers and devices. This is to make sure no one can use any residual information against you. Although losing all your data might seem like a loss, you really have no other choice if it means protecting your privacy or getting compromised. When it comes to business, there will be times when you will need to destroy every data left in your system. This is a way to make sure no company information will be fall on the wrong hands.
Masking Method with Madness
The idea of having to destroy something doesn’t always spark joy. It means you might have to ruin something that took a lot of time and effort to make. In business, there will be times when you will need to switch to new systems and media platforms. This comes with the responsibility of having to erase any remaining information from your old system as to not have it fall to the wrong hands. You can call this method as data destruction.
Data destruction is the process of clearing, eradicating, and making sure that any and all data in a system becomes impossible to reread and reuse. This process helps businesses make sure that no other party can retrieve their files and use them for personal gain.
In an age where almost every business relies on technology to process and store every aspect of their operations, you need to make sure all your data is protected. And when they are no longer relevant, they must also be properly disposed of. It is a smart decision to destroy data that may no longer be needed. This unused information may no longer be relevant to your company, but that doesn’t mean you’re free to share it with anyone. This can still be utilised by other entities for illicit transactions.
The Right Path to Ruin
You may think that secure data destruction is the same as literally destroying your device to get rid of all information. That’s sort of true. But that’s not the only way to do things. You don’t have to go so far as to get your equipment smashed to bits. Plus, there are still tech-savvy individuals who can collect information from the broken pieces of your system.
What you need to do is make sure you leave no traces of your information in your system. Deleting your files from your computer is not enough. You need to follow certain methods to make sure your systems are clean. This is especially necessary when you plan on changing and upgrading your systems. To clean out your system, you need to know the different approaches used for data destruction. Here are some methods used to have a clean system.
Reformatting
Reformatting and deleting files from a device is one of the most basic methods of data destruction. Although it doesn’t really fully erase the file from the system, it is however a good start. After doing this, you may need to do other precautionary measure to ensure that your files are completely erased.
Overwriting Data
Overwriting is the process of covering the code of a certain file with a pattern of ones and zeroes. Overwriting can be done more than once to make sure that the data is really deleted. The pattern you overwrite does not need to be random. Overwriting does work, but it takes quite a while to achieve.
Degaussing
Computers and other devices rely on electricity to function. That is why degaussing is a trusted method for data destruction. This process includes using strong magnets to disrupt the magnetic fields around a device. Although it is effective, it does make your device impossible to reuse.
Physical Destruction
Physically destroying a device will of course get rid of a lot of data. It makes a lot of chips hard to read and not usable. If a device is fully, and completely smashed, you can be sure that no data is saved. This will cost you a lot of money though. And you’ll have to say goodbye to your whole system.
Your information should never reach the wrong people. That is why you should practice secure data destruction. If you don’t think you’re able to handle this on your own, there are professional data destruction services that can help you out.