Organizations store huge quantities of sensitive data on their IT hardware and electronic equipment. Once these devices reach the end of their life, they become a burden to business owners as the need for safekeeping and securing data arises. They fear that confidential information might fall into the wrong hands and affect the organization’s name and reputation. For this reason, they are led to a search for secure IT equipment disposal. Having a proper data destruction policy and secure disposal of IT equipment is necessary for all organizations wanting to securely erase data.
What is Secure IT Equipment Disposal?
Big businesses can choose to just throw their old IT assets away at landfills or at recycling bins near them. This would be disposal but surely won’t be secure. Careless disposal of IT equipment can cause harm to the environment as electronic wastes in landfills won’t do any good to the environment.
More than that, there is a chance of data being stolen from those devices which hamper the credibility of the company and can even mean hefty fines for not complying with the country’s privacy laws. Also, secure IT disposal prioritizes asset recovery and remarketing which could bring money into the company.
Therefore, secure IT equipment disposal refers to the method of disposing of old IT assets and devices in an environment-friendly way and also ensuring all the data from those devices cannot be recovered by any method whatsoever. It involves steps such as creating an asset list, designating their end state, and figuring out the best method for secure data erasure before recycling the electronic waste.
What is the Difference Between IT equipment Disposal and E-waste Disposal?
If you haven’t noticed, we have written a separate blog for Electronic waste disposal and some of you might feel why to cover IT Equipment Disposal on a separate blog altogether. The difference between these terms is a bit technical which I will be mentioning here.
E-waste is an umbrella term that defines all kinds of electronic waste including HDDs, computers, printers, televisions, laptops, cameras, car batteries, or any other electronic components that are deemed unusable. IT Assets on the other hand are those assets that are used by the company on a day-to-day basis for serving customers and facilitating data storage.
These mostly include technical equipment and can also be said electronic waste. Just one major difference is that IT assets refer to e wastes of businesses and data centers while e-wastes are generally used to refer to waste pertaining to both individuals and businesses.
Why Is the Secure Disposal of IT Equipment Important?
While obsolete and damaged IT assets like DVDs, CDs, PCs, smartphones, flash drives, memory cards, and hard drives can be reformatted, erased, wiped, or degaussed, if the physical devices themselves remain intact, it is likely that data can still be retrieved. Moreover, server decommissioning or data center decommissioning can uncover huge volumes of devices and HDDs requiring proper data destruction.
To reduce the risks, secure data destruction should be implemented. For printer disposal, computer disposal, hardware disposal, or any other kind of IT asset disposal, data destruction is the process of ensuring that data on HDDs of disposing of assets is irrecoverable. Let’s take a quick look at some of the importance of proper IT equipment disposal…
Aside from complying with local legislation and ensuring your data remains safe, the secure disposal of IT Equipment has lots of benefits. We’ve listed some of them below:
1. Preserve our natural resources.
Recycled IT hardware components are often reused in the assembly or fabrication of new computers. By extending the use of these components, the need to create new materials like metal and plastic is ultimately lowered.
2. Maximize the value of your outdated IT equipment.
Working with certified IT disposal companies allows you to resell an IT component and maximize its value. The sales returns can offset the asset disposal costs and even return a credit to your business.
3. Avoid unnecessary data risks.
If you don’t work with a certified ITAD company, you might put your company’s data at risk. Millions of dollars are spent on cyber security, it is important to maintain this level of diligence at hardware disposal.
4. Leave a lasting positive impact on the community.
Your old IT equipment might have already served its purpose for your organization, but it may still be useful to others. The secure disposal of your IT assets provides an opportunity to support your community as there are notable benefits of e-waste recycling for the environment as well as the local community. There might be causes headed by charitable institutions that will benefit from a computer donation rather than old computer disposal. Even if the devices aren’t usable, lodging them for IT recycling is ideal for the environment.
How to Safely Conduct IT Equipment Disposal?
Now that you have known about the “What” and the “Why” of IT assets disposal, let’s explore the “How” of safe IT assets disposal. So… how to dispose of IT equipment? There are two major activities that guarantee IT disposal is a secure one- secure data destruction and then recycling. The IT equipment and old computer recycling process is a part of the IT equipment disposal process.

Secure data destruction is the most important process that guarantees data security and prevents any possibility of data theft from discarded devices. Some methods of data destruction such as shredding automatically ensure the disposal of hard drives or other devices. Now, let us see how the data erasure process works as ensuring complete data destruction essentially guarantees secure IT equipment disposal.
How Secure Data Destruction Works?
In the process of disposing of IT equipment and data destruction, several methods can be used. But as for most companies, they use the Blancco data erasure software. It’s among the most secure and trusted software when it comes to getting rid of data.
The use of the Blancco data erasure software includes reporting and allows an opportunity for IT asset remarketing over traditional physical destruction methods. With this software, data sanitization can be achieved and even erased in a live environment without experiencing downtimes.
For old computer disposal or any kind of IT Asset disposal, data destruction ensures that the disposal cannot harm the organization in any way, making the process of hard drive disposal very easy.
In addition, all confidential and personal data are wiped from devices in the most secure way. After that, a certification of erasure is issued per device for legislation compliance.
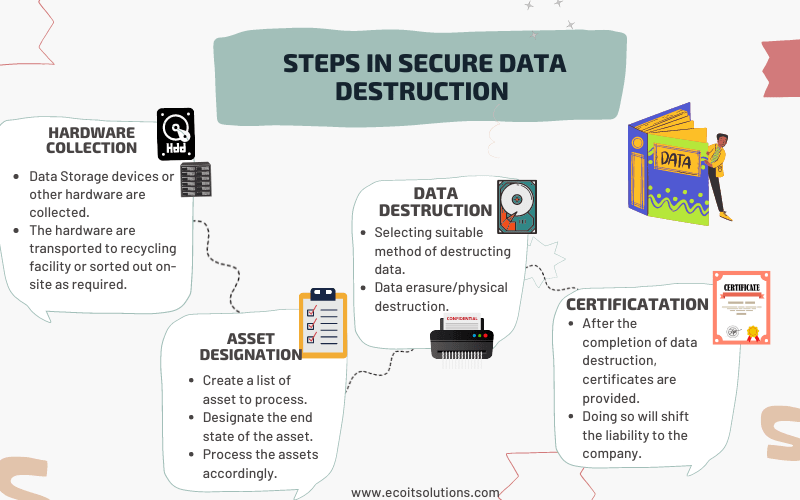
Here’s a quick overview of the inclusions of a secure data destruction service:
- Hardware Collection – The company will arrange a pickup schedule for the collection of your IT equipment.
- Asset list – At this stage, all IT components should have already reached the facility. Now, a list of all IT assets is created, and everything will be sorted accordingly.
- Data Destruction – During the data destruction process, digital and magnetic media, such as discs and hard drives are destroyed. At the end of the process, data can no longer be read or retrieved. This process will be explained further below.
- Certification – The ITAD company then gives a certificate of secure data destruction.
A Closer Look into the Entire Data Erasure Process
Because the data destruction process requires technical expertise, only certified and licensed ITAD companies are allowed to offer secure asset disposal of IT equipment services. But to give you a better idea of what they do here’s a quick overview of the process:
- Fetch the hard disk parameters.
- Test the hard drive for errors. Most of the time, the SMART self-test will be used. But this is only optional.
- Next, write hard disk sectors with specific patterns starting with sector number 0. Count the written errors as they come up as bad sectors.
- Now, the buffers are flushed. Errors will be checked again in this stage.
- If there are multiple overwriting passes specified, steps 3 and 4 need to be repeated. You will notice that the number of bad sectors is multiplied by the amount of overwriting passes.
You may ask, “what if the Blancco data erasure software fails in the process?” Well, that should not be a problem because the concerned device will be destroyed onsite in the company’s secured shredding facility. The device will be shredded into tiny pieces.
When Do You Need a Secure Data Destruction Service?
When is a secure data destruction service needed? There are many instances and situations that call for it. People need to be adept at minimizing e-waste before disposing of every electronic waste rampantly and only disposing of waste after erasing all their data. Perhaps your company’s data are scattered across different systems and you need to reduce your maintenance costs by migrating everything to bigger and more reliable hardware. Or maybe there has been a sudden acquisition of a business, which requires extra hardware for redundant data and applications or requires a change in current working methods.
In such cases, businesses might seek printer disposal solutions, disposal of printer cartridges, or any other asset disposal depending on the kind of changes implemented in the business.
Are you moving offices soon? Then you might want to consider the options to securely get rid of any obsolete IT equipment or choose e-waste recycling services. Many local companies that offer electronic recycling in Australia may assist you with all your office logistics, so there shouldn’t be much of a problem here.
Not only will you have a hassle-free experience when moving to your new office space, you might also earn money from reselling reusable components.
However, if no local electronic recycling facilities serving your area, it is best to find companies that offer ITAD services. They can also assist and help with the logistics.
Why Choose Eco IT Solutions?
There are plenty of companies that offer ITAD and computer recycling in Sydney, but why choose Eco IT Solutions? We make this process easy and hassle-free, convenient for you with 24-48hr collection times.
Our IT asset disposal services are compliant with the data protection legislation and in line with environmentally responsible ISO certifications of 14001, and 9001. You will receive data erasure and responsible e-waste disposal certificates for each batch.
Should you be interested in any of our services, feel free to reach out. Call us at 02 8055 3775 or visit us at Level 3, 11 York St., Sydney, NSW, 2000.
FAQs
[ecoit_faq]


Comments
One response to “What is Secure IT Equipment Disposal? Why Do It? & How to Do It the Best?”
[…] you choose to dispose of your old IT assets instead, the best way to do so is to submit them to a recycling facility. They will be disassembled […]